Three years ago, the tech industry faced the unprecedented challenges of a pandemic-altered world. The rapid rise of hybrid workforces, evolving compliance regulations, and accelerated digital transformation via the cloud created fertile ground for attacks on digital infrastructure. In response, the cybersecurity market surged. The new dynamics and booming market inspired Menlo to release our first cybersecurity checklist, which documented our investment criteria. That checklist was informed by our decades of collective expertise and captured the thinking that led us to investments in industry leaders like Abnormal Security, Obsidian Security, Mimic, and BitSight.
We stand at another pivotal moment today. AI-generated cyber attacks are reaching unprecedented volumes and ever-increasing complexity. In response, we are witnessing the rise of AI-powered security tooling. Earlier this year, we explored these trends in our AI for Security and Security for AI posts. Now, the magnitude of change driven by AI has prompted us to update our cybersecurity checklist for this new AI era and share how we are discovering the next generation of great cybersecurity companies.
1. Cloud-native and AI-native architecture
The most promising cybersecurity startups today aren’t just cloud-native—they’re AI-native. While traditional security measures, even cloud-based ones, struggle to keep up with the speed and complexity of modern cyber threats, AI-native companies are built to handle this challenge from the ground up. These companies are designed to ingest and process vast amounts of unstructured data, enabling them to predict, prevent, and remediate attacks with a precision that human analysts simply cannot match. By building their products with AI at the core—rather than retrofitting AI onto existing systems—AI-native founders avoid legacy constraints, optimizing for performance, accuracy, and speed.
A prime example is Abnormal Security, which is leveraging an advanced AI behavioral model that pinpoints malicious activity by establishing a baseline for “normal” behavior for each specific user. Abnormal’s AI Security Mailbox provides an AI-powered personal cyber assistant for every end user and an AI-powered security help desk coworker for every analyst to automate email security operations.
2. Founding teams with strong security and AI DNA
Pure cybersecurity expertise, while crucial, is no longer sufficient on its own. Now, we’re looking at founding teams that marry deep cybersecurity experience with cutting-edge AI expertise.
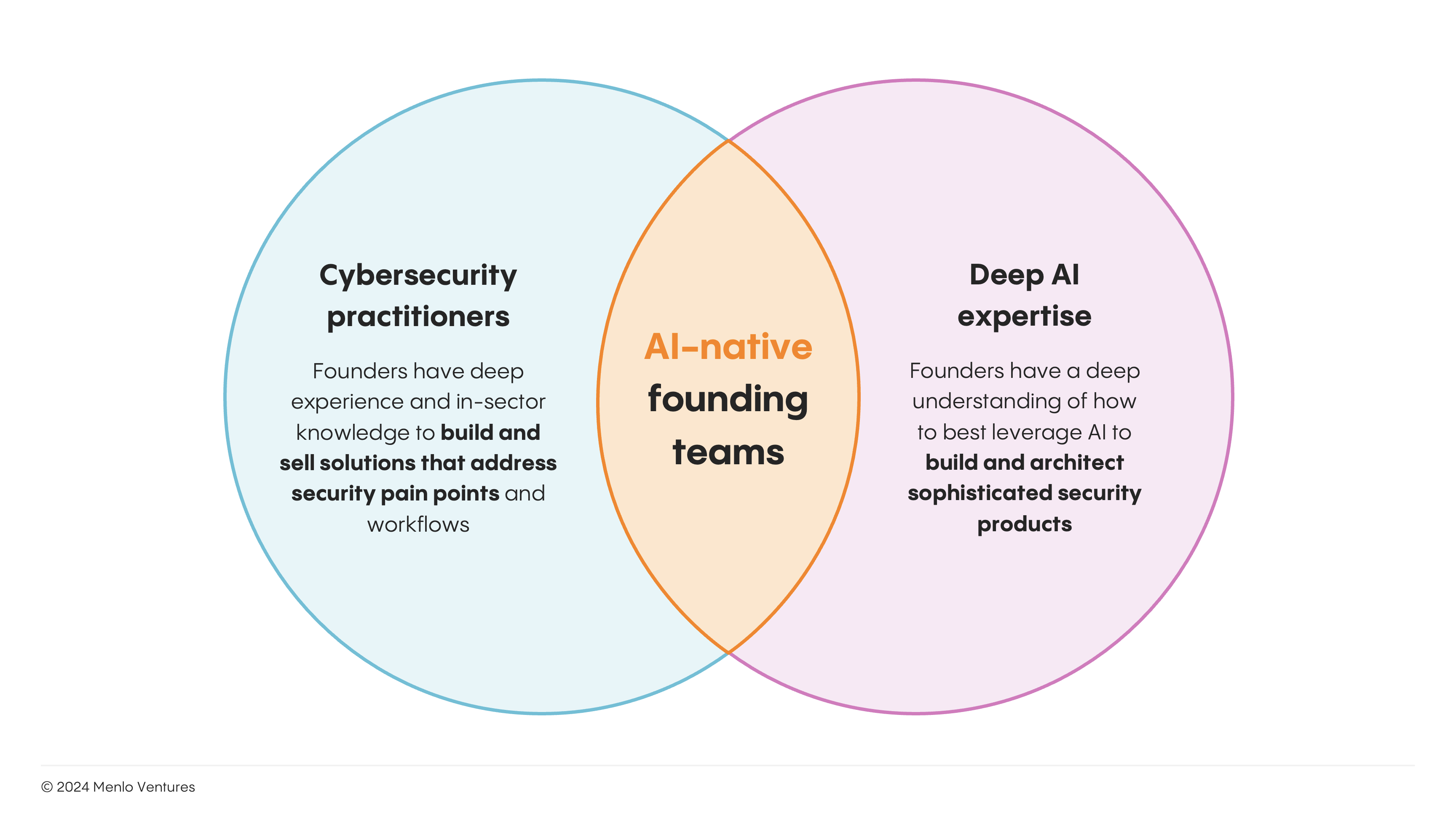
The combination of security and AI DNA among a founding team is crucial for developing solutions that not only understand the nuances of complex security challenges, but can also harness the full potential of AI to solve them. This includes ensuring the product can do the following:
- Scale quickly with vast amounts of structured and unstructured data;
- Work flexibly alongside current and future foundational models;
- Maintain efficient resource utilization; and
- Prioritize explainable AI.
3. Leveraging AI agents to deliver on the Software-as-a-Service promise
The growing cybersecurity talent shortage is estimated at four million professionals globally and is widening by 12.6% year over year. AI-generated security attacks are compounding the pressure on understaffed security teams already plagued by alert fatigue and triage hell. 73% of security professionals report missing, ignoring, or failing to remediate high-priority alerts.
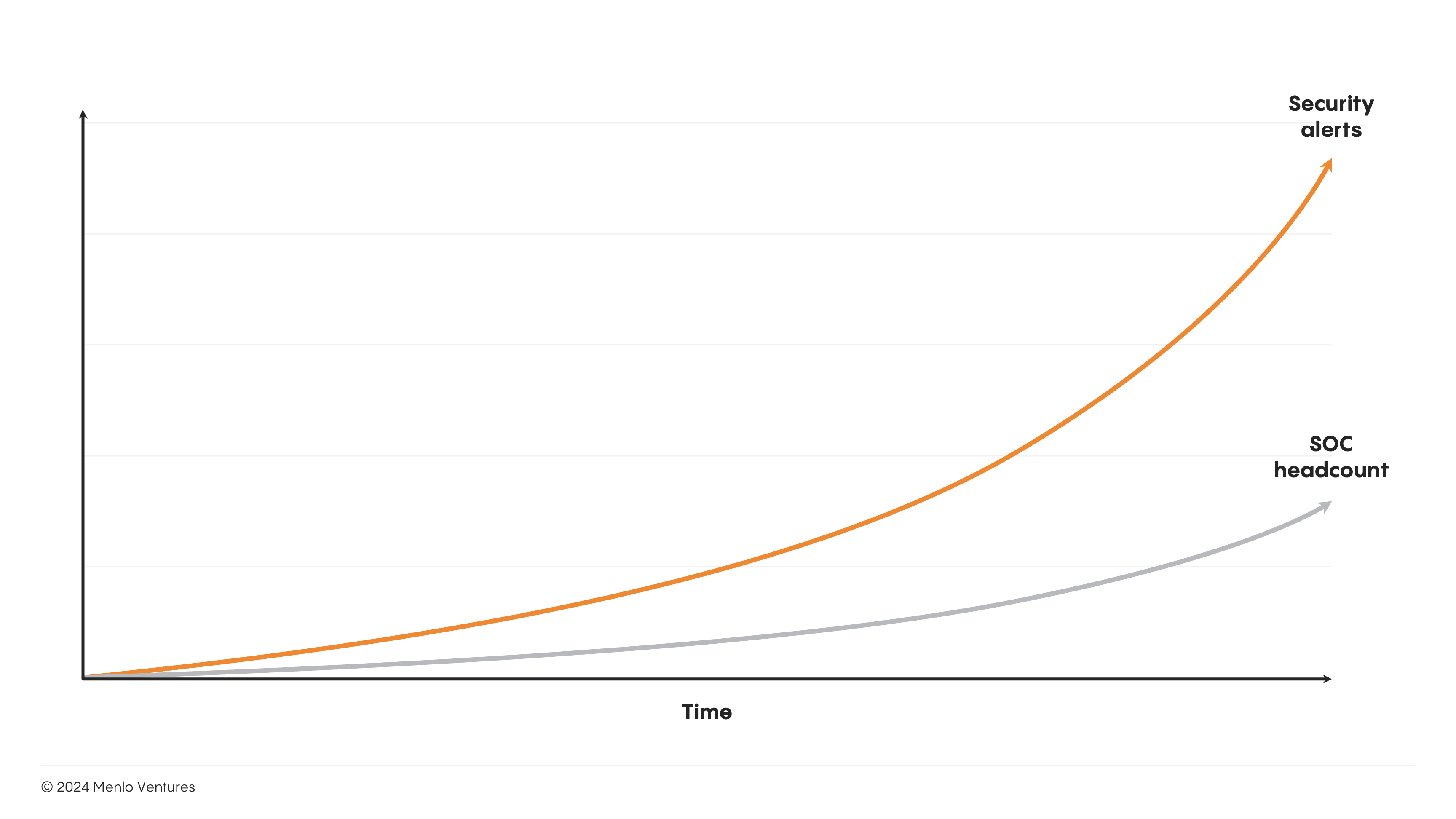
AI is leading a Software-as-a-Service paradigm shift in which AI agents take over end-to-end tasks and automate human workflows. Overall, this is a $4.6 trillion opportunity—one that far exceeds all existing software spend. We are looking for companies leveraging agentic architectures to automate and enhance security operations from SOC automation to AI-driven attack and penetration testing. These new architectures aren’t just filling workforce gaps; they are transforming the way security teams operate.
4. Innovative approaches to data and identity security
As AI proliferates across enterprises, we are looking for companies that are solving the emerging challenges in data security and identity management in an AI-driven world.
- Data security: AI relies on vast amounts of data to deliver value, with models processing and indexing large volumes of both structured and unstructured data across an organization. While granting AI agents access to sensitive data is crucial for improving business outcomes, it also opens the door to potential catastrophic data breaches and privacy risks if not carefully monitored and governed. Simply knowing where your sensitive data is located is no longer sufficient; it’s essential to know which types of data AI agents and tools have access to and set controls around them. In the AI era, data security is emerging as a distinct category that demands specialized, AI-first tools to enable granular governance and management at scale.
- Identity security: The surface area of machine identities, or Non-Human Identities (NHIs), is an order of magnitude larger than the human kind, yet there exists no Okta-like equivalent to manage these identities. This gap has created vulnerabilities that attackers have exploited, including the summer 2023 Microsoft attack that compromised the email accounts of 22 organizations and hundreds of individuals. Properly securing identities across both fronts will be critical, not to mention managing the identities of AI agents that will execute tasks on behalf of us with privileged access.
5. Products that are “dead simple” to use
In a market flooded with complex tools, we are looking for companies that prioritize user experience and transparency. Those that set the standard for what is “easy” distinguish themselves by deeply understanding the pain points of their customers and providing the most frictionless solutions.
For security, “dead simple” use is often accomplished by enabling customers to quickly and seamlessly embed their own processes into the tool. This not only improves user experience, but also drives data collection, enhances model performance, and increases product stickiness. Here, AI is a means to that end. Companies like Semgrep, a next-gen SAST platform, use AI to allow enterprise AppSec engineers to generate rules specific to their companies (i.e., rulesets for security audits) via natural language, lowering barriers to adoption.
Similarly, we commend companies that stem from open-source for this very reason. Open-source offerings provide a greater degree of developer transparency and general openness, allowing enterprise developers and IT leaders to test the product compatibility and performance before writing a check. In light of the black box nature of complex AI models, budget crunches, and broader industry hesitancy towards adopting new AI-first technologies, open-source offerings bridge a much-needed purchasing gap for CISOs.

Think you check the boxes? We’d love to hear from you.
At Menlo Ventures, we remain excited about the future of cybersecurity, particularly companies leading with AI innovation. If you’re building something that aligns with this vision, let’s talk! You can reach out to us at:
Venky is a partner at Menlo Ventures focused on investments in both the consumer and enterprise sectors. He currently serves on the boards of Abnormal Security, Aisera, Appdome, BitSight, Breather, Dedrone, MealPal, Rover, Sonrai Security, StackRox, and Unravel Data. Prior to joining Menlo, he was a managing partner at Globespan…
Rama is a partner at Menlo Ventures, focused on investments in cybersecurity, AI, and cloud infrastructure. He is passionate about partnering with founders to build the next generation of cybersecurity, infrastructure, and observability companies for the new AI stack; his goal is to serve them a trusted advisor, earning the…
As a principal at Menlo Ventures, Feyza focuses on soon-to-breakout consumer, fintech, and enterprise SaaS companies. Prior to Menlo, Feyza worked as an engineer at various companies in different growth stages, including Nucleus Scientific (now Indigotech), Fitbit, and Analog Devices. Her exposure to a wide range of tasks and opportunities…
As an investor at Menlo Ventures, Sam focuses on SaaS, AI/ML, and cloud infrastructure opportunities. She is passionate about supporting strong founders with a vision to transform an industry. Sam joined Menlo from the Boston Consulting Group, where she was a core member of the firm’s Principal Investors and Private…