On March 18 2025, Google announced its intent to acquire Wiz for a jaw-dropping $33B—marking not just the largest cybersecurity transaction in history, but the most valuable venture-backed exit ever recorded. This milestone reinforces a powerful yet consistent pattern in cybersecurity: Every major platform shift—internet, mobile, cloud—has forged a new wave of market leaders. AI is next.
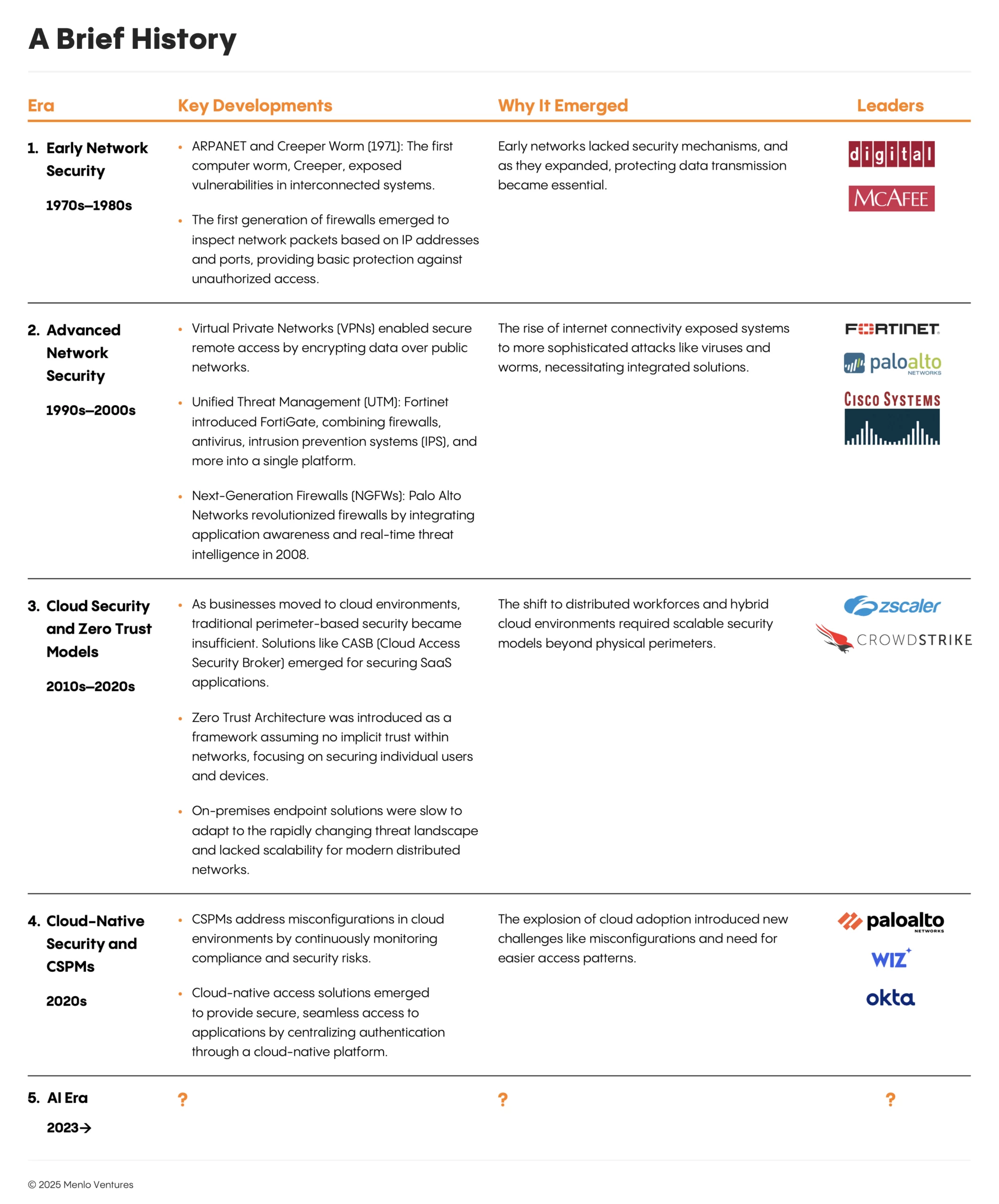
From the dawn of the internet through the cloud transformation, we’ve witnessed multiple $10B+ outcomes as security solutions evolved to protect each new paradigm—Wiz being the most recent example. Now, AI represents the next critical inflection point—not merely an incremental improvement, but a fundamental transformation—of the cybersecurity landscape.
We expect the impact of AI will be twofold: AI will take traditionally moderate-sized markets and scale them up into our next set of $10B+ opportunities. At the same time, AI will compound already substantial markets into new $100B+ mega-markets. Here are our bets on the domains AI will dominate.
Breaking $10B: The Security Markets Poised to Explode With AI
AI Guardrails: Monitoring and Securing Agent Interactions
As AI becomes deeply integrated into enterprise workflows, organizations face a new frontier of risk: the malicious or unauthorized use of AI systems themselves. Firewalls that protect enterprises from AI misuse represent a critical new security category focused on monitoring, controlling, and securing AI interactions.
Expanding the market with AI: As companies rapidly deploy AI, they’re creating unprecedented attack surfaces and risks—from data leakage through prompt engineering to the generation of malicious content. These specialized firewalls monitor AI system interactions, detect unauthorized access patterns, prevent sensitive data exposure, and protect against AI-specific attack vectors like prompt injection.
With nearly every enterprise racing to adopt AI technologies, the need for specialized security controls becomes non-negotiable. The market potential is magnified by regulatory pressures around responsible AI use and the potentially catastrophic reputational damage from AI systems being manipulated to create harmful outputs or expose sensitive information.
Automated Penetration Testing: Continuous Security Validation
Manual penetration testing has been the gold standard for decades, but it suffers from numerous limitations: It’s periodic, expensive, and constrained by human resource availability.
Expanding the market with AI: AI-powered automated penetration testing transforms security validation from a point-in-time assessment to a continuous process. This represents a paradigm shift from “Are we secure today?” to “Are we secure right now?” With organizations deploying code hundreds or thousands of times per day, continuous validation becomes an absolute necessity.
The market potential expands as these solutions begin orchestrating complex attacks at scale across entire enterprise environments, identifying complex attack chains that might otherwise remain hidden. The future belongs to solutions that combine the creativity of human red teamers with the tireless consistency of machines.
AI-Enhanced DLP: Protecting Data in the Age of Information Sprawl
Data Loss Prevention (DLP) has been chronically difficult to implement effectively, with traditional solutions generating excessive false positives and creating significant friction for users.
AI-fueled expansion: As data volumes surge and work becomes increasingly distributed, traditional DLP approaches simply cannot scale. AI-powered DLP solutions will understand the right context, recognize sensitive information across unstructured data, and make intelligent decisions about appropriate data handling.
The massive expansion of unstructured data and the increasing regulatory pressures around data protection create an urgent need that older technologies cannot address. The winners will deliver protection without impeding productivity.
AI Agents for Identity Management
Identity has become the new enterprise perimeter, yet managing identities at scale poses enormous challenges for every organization.
Expanding the market with AI: AI agents will continuously monitor identity behaviors, detect credential compromise, and intelligently manage access rights across complex hybrid environments. As workforces become increasingly distributed and companies adopt more SaaS applications, the identity problem grows exponentially more complex.
The companies that will deploy autonomous agents to manage the entire identity lifecycle while maintaining security and compliance will capture significant market share. The combination of identity sprawl and zero-trust architectures creates perfect market conditions for this category.
AI-Driven Code Security: Shifting Security Truly Left
As organizations rapidly adopt AI code generation tools, they face a significant hidden risk: These models were trained on vast repositories of open-source code, much of which contains vulnerabilities, anti-patterns, and security flaws.
Expanding the market with AI: AI coding assistants are generating billions of lines of code that often perpetuate the security flaws present in their training data. This creates a compound security problem—not only are vulnerabilities being introduced at unprecedented scale, but they’re being propagated across thousands of organizations simultaneously.
The challenge is particularly acute because developers inherently trust AI-generated code (sometimes dubbed an “automation bias”), assuming it represents best practices, when in reality it may reproduce problematic patterns from its training data. This presents a strong opportunity for AI-driven code security solutions like Semgrep* that can identify and remediate security issues in AI-generated code before deployment.
With enterprises now generating up to 80% of new code through AI assistance, the scale of potentially vulnerable code being introduced is staggering. Companies that analyze AI-generated code in real-time, identify inherited security flaws, and suggest secure alternatives will capture enormous value as essential guardrails in the new AI-powered development paradigm.
The winners in this category will deliver intelligent solutions that not only detect vulnerabilities but understand the right context and purpose of code to suggest appropriate secure alternatives, effectively creating a “security firewall” between AI code generation and production environments.
$100B and Beyond: How AI Will Reshape Security’s Biggest Markets
Email Security and Social Engineering Defense
Email remains the primary attack vector for breaches, with social engineering attacks becoming all the more sophisticated and difficult to detect.
Accelerating the market with AI: The scale is staggering—billions of emails traverse corporate networks daily, each representing a potential attack vector. AI solutions like Abnormal Security* can analyze subtle linguistic patterns, detect anomalies in communication styles, and identify sophisticated impersonation attempts that would fool traditional systems.
The market size expands dramatically as these solutions move beyond email to protect all communication channels, including collaboration tools, messaging platforms, and social media. The financial impact of preventing just one major breach can justify the entire investment, creating massive value potential for market leaders.
DSPM: The Imperative of Data Security in the AI Era
As organizations rapidly integrate AI systems into core business processes, data security has transformed from important to existential. AI models trained on or accessing corporate data create unprecedented risks of data exposure, unauthorized use, and regulatory violations.
Accelerating the market with AI: The adoption of AI dramatically elevates the importance of data security in two critical dimensions. First, organizations must comprehensively understand where their sensitive data resides before allowing AI systems to access it. Without this visibility, companies risk exposing proprietary information, customer data, and regulated content through AI interactions. Second, they need robust protection mechanisms to monitor and control how this data is utilized by increasingly autonomous AI systems.
The convergence of Data Security Posture Management (DSPM) and Data Loss Prevention (DLP) addresses this urgent need. DSPM provides the critical foundation—discovering, classifying, and mapping sensitive data across complex environments—while DLP delivers the enforcement mechanisms to prevent unauthorized access or exfiltration.
What makes this a $100 billion opportunity is the universal nature of the problem. Every organization leveraging AI must first address its data security challenges or risk potentially catastrophic consequences. As generative AI becomes integrated across enterprises, the ability to definitively answer “What data can this AI system access?” and “How is this data being used?” becomes non-negotiable.
The winners in this category will create unified platforms that provide complete visibility into sensitive data location, context-aware classification, and intelligent protection that balances security with the practical needs of AI-driven innovation. As AI systems become increasingly autonomous and pervasive, these solutions will evolve from security tools to essential infrastructure for responsible AI deployment.
Identity and Data: The Nexus of Modern Security
Identity and data security are increasingly interconnected—understanding who should have access to what data and ensuring appropriate controls represents the core of modern security architectures.
Accelerating the market with AI: The explosion of digital identities (human and non-human) combined with the exponential growth of data creates a perfect storm of complexity. Companies like Astrix Security* leverage AI to understand the relationships between identities and data, continuously validate access appropriateness, and automatically remediate issues represent the future of security.
This market spans every organization with sensitive data and becomes increasingly critical as zero-trust architectures become the standard. By addressing both identity and data, these solutions protect the two most critical elements of modern digital infrastructure.
SOC Automation: Addressing the Cybersecurity Workforce Crisis
The global cybersecurity industry faces a staggering workforce crisis—approximately 4.7 million cybersecurity professionals currently employed worldwide with an estimated 3.4 million unfilled positions. Security Operations Centers (SOCs) in particular suffer from severe staffing shortages while facing exponentially growing threat volumes.
Accelerating the market with AI: The cybersecurity talent gap cannot be bridged through traditional hiring and training alone. AI-powered SOC automation represents the only viable solution to this structural market problem—enabling organizations to detect, investigate, and remediate threats despite persistent workforce constraints.
For example, Crogl’s* agentic AI systems transform SOC operations by intelligently diagnosing cybersecurity threats with human-like reasoning capabilities but machine-scale processing power. These autonomous agents conduct complex threat investigations, contextualize alerts across disparate systems, and execute remediation playbooks with minimal human intervention.
The market potential is extraordinary because these solutions address an existential business problem: Organizations simply cannot hire enough qualified security professionals to manage the threat landscape. By automating up to 80% of routine SOC tasks, these solutions enable human analysts to focus on strategic security challenges rather than drowning in alert triage and incident response.
What makes this a $100B category is its universal applicability—from Fortune 500 enterprises to small businesses, every organization with digital assets needs security operations but cannot staff them adequately. AI-driven SOC automation simultaneously reduces costs while improving security outcomes—a rare combination that creates compelling ROI even in constrained economic environments.
The winners in this space will create autonomous security operations platforms that reliably handle entire classes of threats independently while providing clear explanations of their findings and actions to human supervisors. These solutions will not merely supplement analyst productivity, but provide fully-autonomous security operations at machine scale and speed.
The AI-Driven Future of Cybersecurity
The integration of AI into cybersecurity changes what’s possible. The markets outlined above represent massive opportunities for startups that can execute effectively, delivering intelligence and automation at scale.
For cybersecurity investors and entrepreneurs, these categories represent unprecedented opportunities. The future belongs to those who not only adapt to this shift, but actively drive it forward.
The race is on. Who will take the lead?
*Backed by Menlo Ventures
Venky is a partner at Menlo Ventures focused on investments in both the consumer and enterprise sectors. He currently serves on the boards of Abnormal Security, Aisera, Appdome, BitSight, Breather, Dedrone, MealPal, Rover, Sonrai Security, StackRox, and Unravel Data. Prior to joining Menlo, he was a managing partner at Globespan…
Rama is a partner at Menlo Ventures, focused on investments in cybersecurity, AI, and cloud infrastructure. He is passionate about partnering with founders to build the next generation of cybersecurity, infrastructure, and observability companies for the new AI stack; his goal is to serve them a trusted advisor, earning the…
As a principal at Menlo Ventures, Feyza focuses on soon-to-breakout consumer, fintech, and enterprise SaaS companies. Prior to Menlo, Feyza worked as an engineer at various companies in different growth stages, including Nucleus Scientific (now Indigotech), Fitbit, and Analog Devices. Her exposure to a wide range of tasks and opportunities…
As an investor at Menlo Ventures, Sam focuses on SaaS, AI/ML, and cloud infrastructure opportunities. She is passionate about supporting strong founders with a vision to transform an industry. Sam joined Menlo from the Boston Consulting Group, where she was a core member of the firm’s Principal Investors and Private…