The public cloud markets may have been dreary outside last week, but under the soaring skylight of Moscone Center in San Francisco—host to this year’s RSA Conference, one of the cybersecurity industry’s largest annual gatherings—the convention floor was pulsing with excitement.
And why not? Cybersecurity, as a category, was coming off its most prolific year ever. According to Pitchbook, investors wrote a record $26.4 billion in checks for cybersecurity companies in 2021, a 2.4x increase over the previous year. Since January of last year, 36 companies raised rounds of $200 million or more, including Menlo Ventures portfolio company Abnormal Security, most recently valued at $4 billion.
The funding environment reflects the exponential growth in opportunity in the last decade for the industry. Today, cyberattacks are at an all-time high, and hostile actors target critical sectors across all geographies. Just in the past few years, hackers shut down key US fuel conduits in the Colonial Pipeline attack, took down IT in various New Zealand elementary schools, and shuttered the booking system for Ireland’s national healthcare service. Cybersecurity is no longer just a competitive advantage for organizations—it’s an existential necessity and a top spending priority for CIOs.
Off of these tailwinds, the past decade has already minted a new guard of large, independent security giants. Crowdstrike, Cloudflare, and Splunk are just a few of this new generation to go public in the last few years and are already among the world’s largest cybersecurity companies by market capitalization.
Even the recent market pullback couldn’t put a damper on the mood. While the looming question for all cloud companies has been whether or not a potential recession could constrict budgets and slow revenue growth, industry participants indicated that cybersecurity could be an area of resiliency amid a broader SaaS downturn.
Amid this backdrop, Menlo will continue actively partnering with early-stage cybersecurity companies in the months ahead. Our investment thesis is underpinned by three key macro themes that we heard echoed again and again by security buyers and practitioners at RSA this year.
1. Security budgets are large and will continue to grow this year
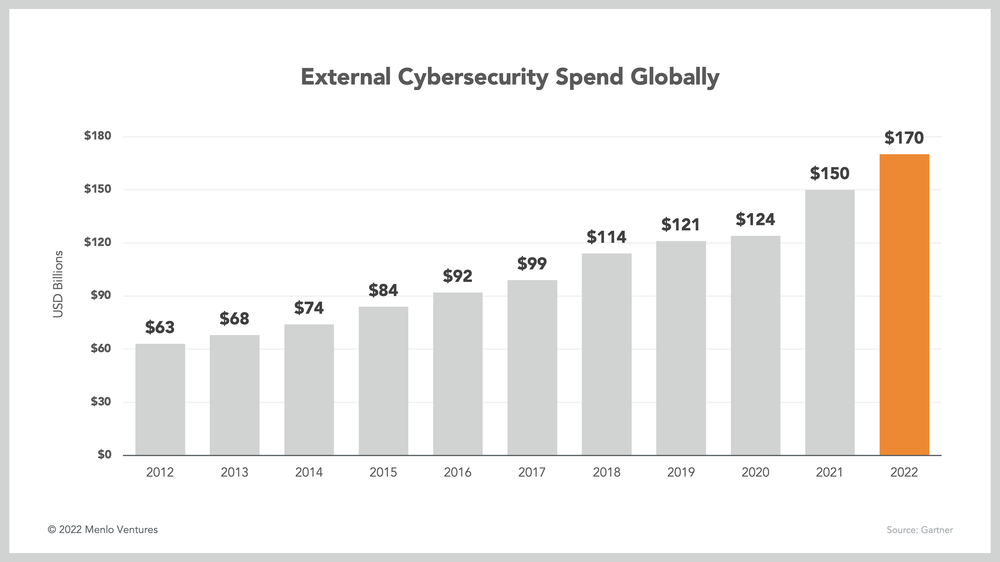
Cybersecurity is a massive and growing market. Spend on third-party solutions totaled $150 billion in 2021 and is expected to top $170 million by year-end, according to several research reports released at this year’s RSA Conference.
This rapid expansion reflects cybersecurity’s rise in priority on the CIO agenda. For a long time, security budgets had been stable at approximately 5% of total IT budgets. But for the past few years, growth in spend on security solutions has begun to outpace that of other software solutions. Going forward, this trend is only expected to further accelerate. In 2022, security budgets are expected to increase 10-13% YoY, as compared to 4-5% YoY for total IT budgets.
This growth in share of budget—as opposed to growth with IT budgets—is important as concerns grow about a broader economic slowdown that may lead to frozen IT budgets and forced rationalizations.
Industry experts see cybersecurity as more resilient to potential cuts than other software because of the newfound prominence that security solutions have found at the board level, and an evolving perception of security as a revenue driver rather than a cost center.
After all, 88% of boards of directors now view cybersecurity as a business risk rather than a technology risk. Major security events like the SolarWinds attack or the Log4J vulnerability have driven the point home: Rising frequency and scale of attacks are necessitating increased defenses, to the point where demonstrated security competency—including data security and privacy, incident response, and strict compliance—are now table stakes for winning new business.
2. Security stacks will continue to evolve: from networks and devices to data and applications

As enterprises have moved to the cloud and workforces have become global and distributed, the traditional security model—focused on robust network and device security aimed at hardening the corporate perimeter against external threats—has given way in recent years to data and application security, both in run-time environments and during development.
At run-time, data protection will be the central focus in the modern security organization’s strategy. The difficulty with data security is that it can be breached through all sorts of vulnerabilities. Misconfigured cloud environments, employees’ poor password hygiene, and leaks of secrets in source code are just a few ways that attackers can quietly access, steal, or destroy large volumes of data assets.
More and more organizations are therefore aiming to secure and monitor their data directly, creating new opportunities for security solutions focused on data protection and encryption services—a trend only further accelerated by regulations such as GDPR.
One especially promising trend Menlo has seen in this space is the move to zero-trust security models. Zero-trust security systems are able to constantly verify identity and access privileges in order to catch cyberattacks more quickly and limit their blast radius. In their move toward zero-trust, organizations should adopt micro-segmentation of networks, much more granular perimeter enforcement, multi-factor authentication, and strict least-privilege access protocols.
Meanwhile, the push to integrate security during development in order to prevent vulnerabilities and data breaches before they happen has catalyzed another promising trend in security investments. The “shift left” approach to security aims to break down silos within engineering organizations, involving software development teams in the cybersecurity process as much and as early as possible. Successful DevSecOps pipelines aim to prevent attacks such as the SolarWinds hack, in which attackers inserted malicious code into a software update.
“Shift left” has been a prominent conversation topic in the security community for a few years, but many organizations still suffer from gaps in collaboration between developers and security teams. In tech organizations without strong DevSecOps pipelines, security reviews are done manually and separately from developers, creating unforeseen delays when issues are found. By directly involving devs in the security process, organizations can ship faster and more securely. Especially with such a shortage of cybersecurity talent in the market, it’s crucial for security organizations to get buy-in and collaboration from developers.
Security organizations aiming to shift left should consider investing in tools that help engineering organizations integrate security into software engineering practices without slowing down developers. Automated security and compliance testing will be key use cases to address, as is code scanning for leaks of secrets and PII. DevSecOps tooling can help drive a necessary culture shift among developers who may not be used to prioritizing security. Increased collaboration between developers and security professionals will be necessary for organizations to consistently ship clean and secure code.
3. Tool overload and a talent shortage will make winners out of end-to-end solutions and security automation
Today, there is a point solution for every security need. But this thriving startup ecosystem is driving a new set of challenges for security practitioners: CISOs don’t have the bandwidth to keep up with all the new options. Moving forward, it will no longer be enough to offer a best-of-breed point solution. Instead, the new imperative will be to consolidate, connect, and automate other siloed security solutions to help stretched security teams with scarce time and resources focus their time and efforts on only the most high-priority threats.
Indeed, in the boom of the last few years, CISOs’ well-intentioned aim to invest heavily in cybersecurity tools has created information overload for SOC teams. The average SOC analyst has to toggle between at least 15-20 security tools every day, with some organizations deploying over 100 different solutions. Investing in too many different tools can create potentially dangerous information silos for security teams. Security vendors who can serve various use cases with multiple modules will address this need and create lucrative upsell opportunities.
Regardless of how comprehensive a single security vendor’s platform claims to be, security teams will inevitably have to integrate various tools to achieve a comprehensive security strategy. Extended Detection Response (XDR), a relatively new framework for unifying a suite of security tools into an effective threat detection, investigation, and response (TDIR) workflow, was top of mind for many security professionals at the conference. XDR architecture aims to integrate SIEM, EDR, and SOAR solutions to connect and analyze data from disparate sources.
In the four years since Nir Zuk of Palo Alto Networks coined the term, XDR has become a priority—it topped the investment priority list in a recent VMWare survey of financial sector CISOs. Tools that help security organizations achieve an integrated, comprehensive, and intelligent security workflow will be highly valuable in the current environment.
CISOs are also dealing with a shortage of cybersecurity talent in the labor market, making purchasing the right cybersecurity solutions to enable lean teams all the more important. Security automation is top of mind for security professionals looking to improve productivity and response times. Automated security workflows help security teams respond to common threats more quickly, help large organizations standardize security and compliance practices, and free up analysts to focus on higher-value activities. No-code security workflow builders like Torq and Tines have the potential to provide a ton of value to lean security teams.
Conclusion: Toward continued cybersecurity growth
Despite uncertain market conditions, it was clear at RSA that cybersecurity will remain a strong investment category, and Menlo Ventures is looking to be an active partner to the most promising companies in the space. Our existing portfolio consists of a number of market leaders already working toward some of the trends mentioned above, including Abnormal Security, Appdome, BitSight, Cequence, Dedrone, Immersive Labs, Obsidian Security, Sonrai Security, StackRox, and Strata.
To learn more about how Menlo is thinking about the cybersecurity market, be sure to read Menlo Ventures’ Cybersecurity Checklist.
As an investor at Menlo Ventures, Derek concentrates on identifying investment opportunities across the firm’s thesis areas, covering AI, cloud infrastructure, digital health, and enterprise SaaS. Derek is especially focused on investing in soon-to-be breakout companies at the inflection stage. Derek joined Menlo from Bain & Company where he worked…







